BSIMM8 study reinforces benchmarking as a critical exercise in early stages of software security initiatives

Synopsys, Inc. released BSIMM8, the latest version of one of the industry’s leading descriptive software security maturity models, which is based on real-world data and helps organisations plan, execute, and measure their software security initiatives (SSIs).This latest iteration of the Building Security in Maturity Model (BSIMM) study is based on data collected from the largest community to date. BSIMM8 shows that software security is becoming a critical business priority with more organisations benchmarking their efforts early in their SSI lifecycle and using the results strategically to improve their risk posture over time.
“With the rise of widely distributed and increasingly disruptive attacks targeting vulnerable software, we’re seeing a shift from the reactive ‘penetrate and patch’ approach toward more proactive strategies that empower organisations to build secure software systematically from the ground up,” said Dr. Gary McGraw, vice president of security technology at Synopsys.
“Organisations are beginning to understand that they can mitigate risk more effectively by establishing a software security initiative, assessing their strengths and weaknesses early on through instruments like the BSIMM, and focusing their efforts on the most appropriate practices and activities.”
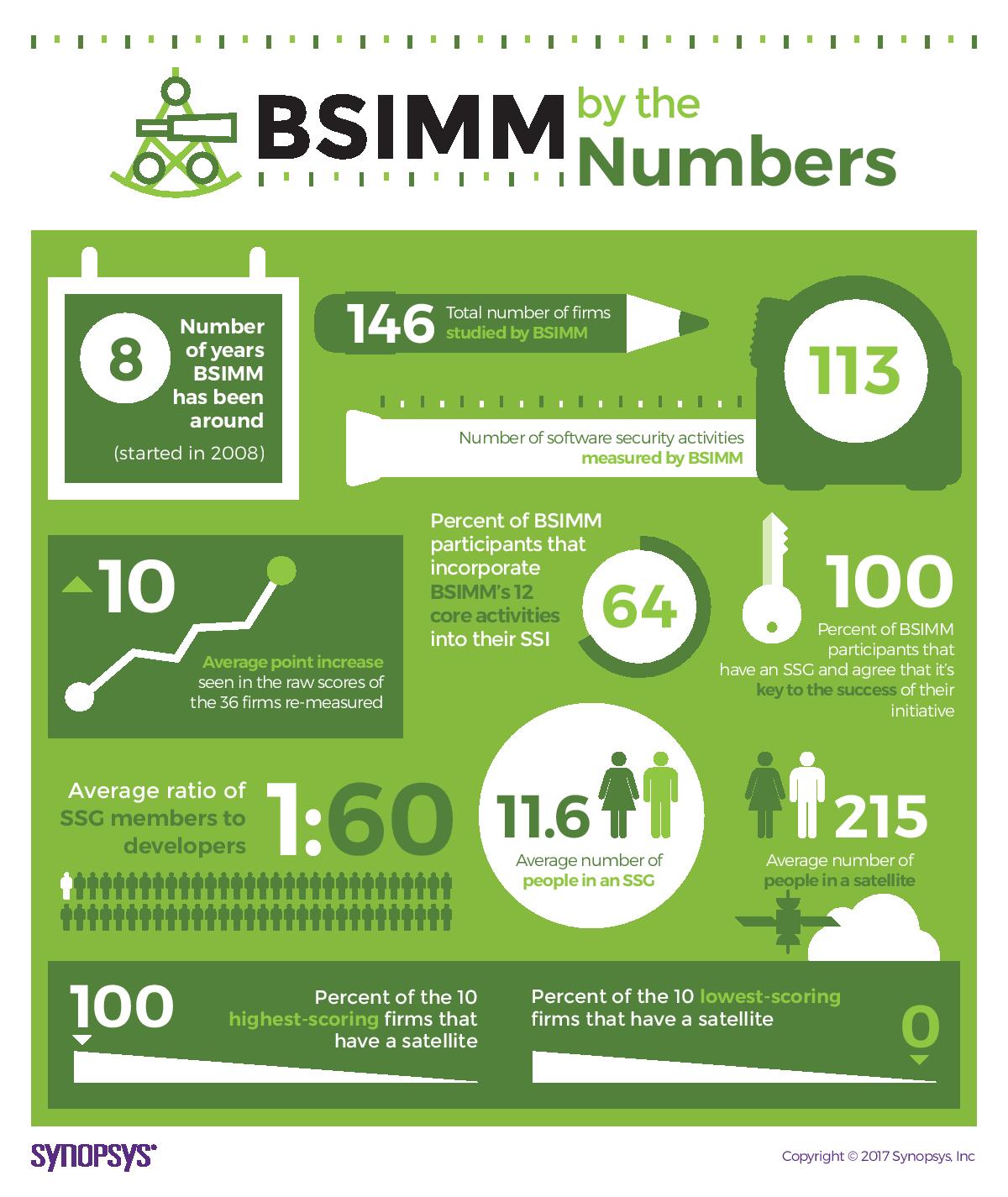
BSIMM8 includes data collected from 109 firms and describes the work of 4,769 software security professionals. Their work guides and maximises the security efforts of almost 300,000 developers across approximately 95,000 applications. BSIMM8 firms represent industry verticals including financial services, independent software vendors (ISVs), cloud, healthcare, Internet of Things (IoT), and insurance.
Key findings from the BSIMM8 study:
- Organisations use the BSIMM to jumpstart their SSIs. BSIMM8 introduces firms in the early stages of the SSI lifecycle, as evidenced by a slight decrease in the average maturity score (33.1, down from 33.9 in BSIMM7) and average software security group age (3.88 years, down from 3.94 in BSIMM7) of the BSIMM population. SSI benchmarking is one of the pivotal first steps in the software security journey.
- BSIMM firms mature over time. Firms that have participated in multiple BSIMM assessments show a clear trend of improvement, with scores increasing by an average of 10.3, or 33.4%. Benchmarking is an effective exercise in guiding organisations along the optimal path toward building secure software consistently.
- Maturity varies by industry. Each industry prioritises certain activities over others, and every industry and individual organisation has a different path toward building security in. On average, cloud, financial services, and ISV firms are more mature than firms in healthcare, IoT, and insurance. Financial services and cloud firms have notably higher scores in compliance and policy practices, while IoT firms have the most mature software environment practices.
According to Gartner, “Application security requires a structured, programmatic approach to deal with the seeming chaos of new technology and an evolving threat landscape. A successful application security program must be a balanced combination of people, process, and technology.”1
The BSIMM observes firms that have established real software security initiatives, quantifying the occurrence of 113 activities to show the common ground shared by many initiatives as well as the variations that make each initiative unique. The BSIMM data show that high-maturity initiatives are well-rounded—carrying out numerous activities in all 12 of the practices described by the model. Organisations can use the BSIMM to compare initiatives and determine which additional activities might be useful.
To download the report, click here.
Comment on this article below or via Twitter @IoTGN
