Evaluating the security of an enterprise IoT deployment at Domino’s Pizza

Deral Heiland of Rapid7
Recently, I had a great opportunity to work with Domino’s Pizza to evaluate an internally conceived Internet of Things (IoT)-based business solution they had designed and deployed throughout their US store locations.
The goal of this research project, says Deral Heiland, principal security research (IoT) at Rapid7, was to understand the security implications around a large-scale enterprise IoT project and processes related to:
- Acquisition, implementation, and deployment
- Technology and functionality
- Management and support
Laying the groundwork
I sat down with each of the internal teams involved with this project, and we discussed those key areas and how security was defined and applied within each. I gained valuable new insight into how security should play into the design and construction of a large IoT business solution, especially within the planning and acquisition phases. This opportunity allowed me to see how a security-driven organisation like Domino’s approaches a large-scale project like this.
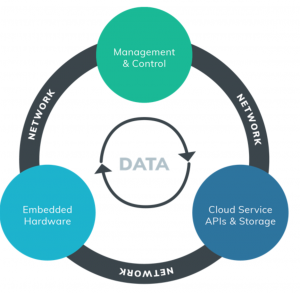
I walked away from this phase of the project with some great takeaways that should be considered on all like-minded projects:
- Always consider vendor security in your risk planning and modeling
- Security “must-haves” should map to your organisation’s internal security policies
Assessing the security status quo
Also, as part of this research project, I conducted a full ecosystem security assessment, examining all the critical hardware components, operation software, and associated network communications. As with any large-scale enterprise implementation, we did find a few security problems.
This is the main reason all projects, even those with security built in from the start, should go through a wide-ranging security assessment to flush out any shortcomings that could be lurking under the hood. Once completed, I delivered a comprehensive report, which the security teams and project developers then used to quickly create solutions for fixing the identified issues.
This also allowed me the chance to observe and discuss the processes and methodologies used by this enterprise organisation for building and deploying fixes into production and doing that in a safe way to avoid impacting production.
During a typical security assessment of an enterprise-wide business solution like this, we are reminded of a couple key best-practice items that should always be considered, such as:
![]()
- When testing the security for a new technology, use a holistic approach that targets the entire solutions ecosystem.
- Conduct regular testing of documented security procedures security is a moving target, and testing these procedures regularly can help identify deficiencies.
Bringing the idea to life
Once an idea is designed, built, and deployed into production, we have to make sure the deployed solution remains fully functional and secure. To accomplish that, we moved the deployed enterprise IoT solution under a structured management and support plan at Domino’s. This support structure was designed as expected to help avoid or prevent outages and security incidents that could impact production, loss of services, or loss of data, focusing on:
- Patch management
- Risk and vulnerability management
- Monitoring and logging
Again, it was nice to sit down with the various teams involved in the support infrastructure and talk security and to also see how it was not only applied to this specific project, but how the organisation applied these same security methodologies across the whole enterprise.
During this final evaluation phase of this project, I was reminded of one of the most critical takeaways that many organisations unlike Domino’s, who did it correctly fail to apply: When deploying new embedded technology within your enterprise environment, make sure the technology is properly integrated into your organisation’s patch management.
At the conclusion of this research project, I took away a greatly improved understanding of the complexity, difficulties, and security best-practice challenges a large enterprise IoT project could demand. I was pleased to see, and work with, an organisation that was up to that challenge and who successfully delivered this project to their business.
If you’d like to read more detail on this security research project, check out my report here.
The author is Deral Heiland, principal security research (IoT) at Rapid7.
Comment on this article below or via Twitter @IoTGN
