Can the principles of Zero Trust be applied to IoT?

Stuart Mitchell of ZARIOT
The perception that security has never been a core component or key consideration for the Internet of Things (IoT) has even been highlighted in the familiar joke: ‘the ‘S’ in IoT stands for security. Yet with tens of billions of connected devices, the safety and financial implications of even small security breaches can be vast, as has already been demonstrated by the likes of the Mirai botnet which compromised over half a million IoT devices.
Furthermore, says Stuart Mitchell of ZARIOT, there is much-warranted concern that ‘unless security concerns are comprehensively addressed and trust enabled then IoT’s full potential will not be realised’. A Zero Trust methodology can be comprehensively applied to address and tackle all layers of threat to an IoT project.
Malicious unless certified as safe
As the name implies, Zero Trust assumes all interactions are malicious unless explicitly certified as safe. The methodology evolved in corporate IT, but is arguably more important in IoT security where it has been asserted that the average IoT device will be attacked within only minutes after being connected. The more traditional application of perimeter security allows trust between all those within the perimeter. Zero Trust, on the other hand, customises protection for each individual asset according to its requirements and by mitigating possible attack vectors identified through methodical assessment. By securing each device separately, if any of these assets is compromised the security breach is contained and does not extend to others within the network.
The type and application of IoT devices is hugely varied, as is the way in which these devices use networks to connect and communicate. For example, a connected car requires global and continuous connectivity, high data volumes and can be accessed sporadically. A smart meter requires fixed-location and predictable connectivity, very low data volumes and remote access. A tracked shipment requires regional and periodic connectivity, relatively low data volumes and can be accessed often. Security breaches to any of these can be catastrophic and costly – in different ways, but as a result of the same threats.
Managing security by usage, needs and threats
The Zero Trust approach manages the security of each and every device according to its usage, needs and possible threats. A detailed analysis of any IoT deployment can be carried out by looking at who, what, when, where, why and how the devices are going to be used and what the corresponding attack vectors are. These threats are then eliminated by applying Zero Trust principles accordingly. There are many models, but the following principles, provided by the UK National Cyber Security Centre are very accessible for designing an IoT Zero-Trust architecture.
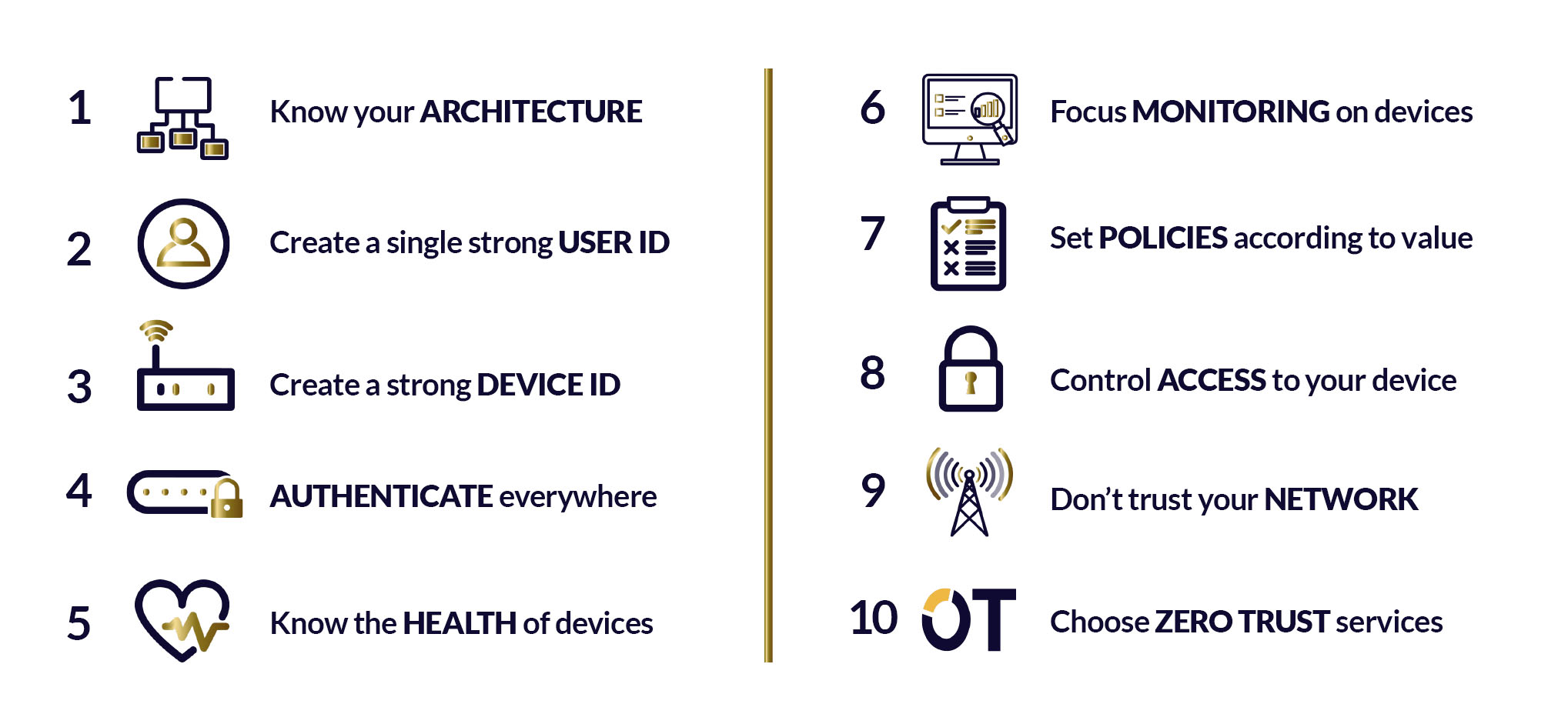
For example, when do you trust your device to connect? As outlined earlier, a connected car may need to be connected constantly, but a smart meter may only need to be connected the first hour of each month. If the trusted time framework of a device is known, the appropriate protection can be provided. Through applying the Zero Trust key principle of “setting policies”, time-based controls can be imposed to restrict connectivity to when it is needed, thereby reducing the likelihood of attack. If a device doesn’t need to be connected all the time, it shouldn’t be.
Similarly when asking who you trust, consideration must be given to who the network trusts. We’ll use cellular as an example, however all network types from 2G to Wi-Fi have vulnerabilities and security concerns. While much attention has been given to protecting the Internet Protocol (IP) layer, protecting the mobile network infrastructure has been overlooked in relation to cellular IoT devices and connectivity. The inherent and inherited vulnerabilities of the mobile network leave it wide open to a number of threats and attacks such as denial of service (DoS), privacy breaches and fraud. Hackers are well acquainted with these access points of cellular networks.
Reliable smart data
A connected car needs to maintain its connectivity for mapping data however it is also necessary to ensure that the location of the car cannot be tracked by bad actors through its SIM. Smart meter data needs not just to arrive, but to be reliable with guarantees that it has not been altered in any way. Application of the Zero Trust principles would focus on “monitoring” the devices and “choosing zero trust services”. The best way to protect the cellular connectivity of IoT devices is with a dynamic, expertly-maintained signalling firewall. It is therefore crucial to ensure that the device is using a SIM from a mobile operator that has a signalling firewall in place in order to restrict unauthorised access to the network itself.
Such analyses on what can and must be trusted are carried out across all aspects of an IoT deployment, from device to SIM to the online services, and Zero Trust principles then applied to minimise the attack surface over each possible attack vector. As IoT projects and products develop across all industries – from smart cars to time-critical medical devices – and as networks evolve, it is essential to adapt to and grow with changing needs, demands and threats, all while placing connectivity security at the fore. A Zero Trust methodology in connectivity is the most effective way to facilitate this and to provide a fully secured IoT solution for the lifetime of an IoT device, no matter its application.
The author is Stuart Mitchell of ZARIOT.
Comment on this article below or via Twitter @IoTGN
