Three reasons you need ITAM for the Internet of Things

Marcel Shaw, federal sales engineer LANDESK
It was 1984, and I was off to the only movie theatre in the town where I lived. The movie was called Terminator and although it was science fiction, the story line had an eerie ring of truth. It was about intelligent computers rising and rebelling against its human progenitors.
This movie introduced many of us to the concept of the internet 10 years before it started to become part of our lives.
Soon after we started connecting personal computers and laptops to the internet, smartphone and tablet technology took root and were mainstream by 2010. Today we are witnessing another major shift in technology with the Internet of Things (IoT), says Marcel Shaw, federal sales engineer at LANDESK.
How do you choose what to manage and what not to manage for IoT?
With the increased number of smart devices coming online, the question becomes what smart devices do we track and how do we track them? Many organisations are still figuring out how to implement ITAM with BYOD.
Therefore, an ITAM solution for IoT might not be on the radar for many organisations; however, a strategy should be considered for the following reasons:
- To control inventory
- To control access
- To provide security
Control inventory
When assets are tracked, information about purchase dates, warranty, and lifecycle states help to control the inventory of the assets. Organisations must decide which smart devices should be tracked using an ITAM solution. For example, should the ITAM solution track a smart light bulb? It might not make sense to track just one, but it could make sense to know how many smart light bulbs are owned and where they are installed.
Furthermore, if there is a software package that controls smart light bulbs, a relationship could be created linking the application to the light bulbs and to an associated software entitlement license. For IoT, I believe it is more practical to manage the contracts, licenses, and vendor information in the ITAM database versus tracking each smart device individually.
One could also argue that smart light bulbs are not considered IT assets and should be managed by facilities’ systems. However, the line between facilities and IT becomes blurred when smart light bulbs are controlled by an application that requires a software license.
Control access
Relationship management is an important part of an ITAM strategy. Relationships are also very important in the context of IoT. Not only does an organisation need to know which devices to connect to their systems, they need to control access between IoT devices and other IoT entities, IT assets, applications, and people.
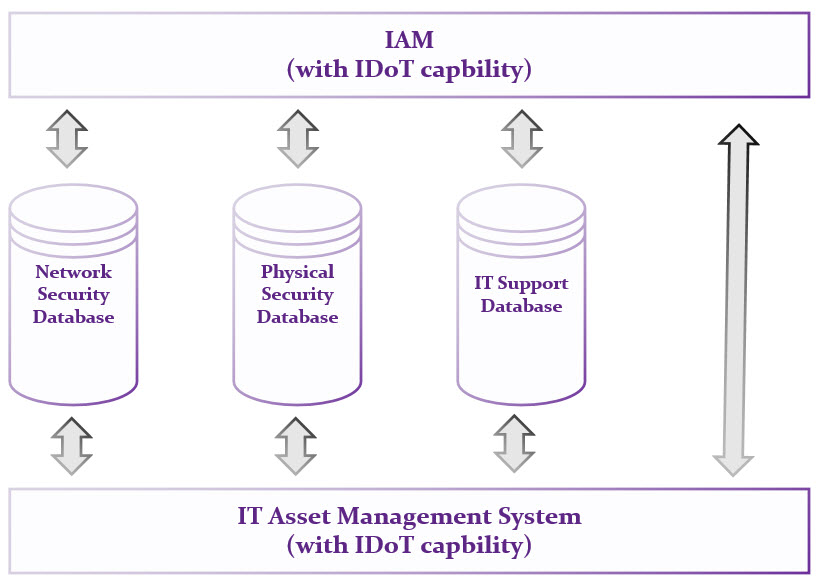
Access to systems and applications is provided using Identity and Access Management (IAM). However, traditional IAM solutions are not capable of dealing with the relationship and access requirements that come with IoT. Therefore, the Identity of Things (IDoT) is an extension of IAM that applies a unique identifier (UID) to IoT devices/objects, which allows you to control relationships and access between IoT and other entities inside and outside of your organisation.
Provide security
The National Cybersecurity Center of Excellence (NCCoE) is addressing IT asset management for the financial services sector.
IoT security is an evolving endeavour to provide security to all devices connected to the internet. Security experts have warned of the potential risk of large numbers of unsecured devices connecting to the Internet since the IoT concept was first proposed in the late 1990s.
Smart light bulbs in the home are a great way to save energy, and smart vacation settings turn lights on and off in different rooms to make it appear someone is home. Smart criminals, such as organised crime or cyber-criminals, could hack your system and learn your vacation programs, thus alerting them that you are on vacation.
They could then sell that information to street criminals informing them of who might be out of town in that criminal’s area. From this example, it is clear that organisations need to apply security to IoT devices so that access is denied to unauthorised users, devices, and malware.
ITAM will provide inventory information to a security system. Without the inventory information, an organisation might not be aware of existing connected IoT entities and their potential security risk. If you don’t have an inventory of all devices connected to the internet, then you don’t have a complete security solution. In my opinion, the lines between ITAM and security will continue to disappear; meaning, that one day, complete security solutions will not exist without an ITAM solution in place.
The good news so far is that Skynet is not yet self-aware which, if you are familiar with the movie Terminator, signaled the beginning of the rebellion against humans. We might not be facing a threat from intelligent interconnected computers waging war on the human race; however, we do face threats from other countries, criminals, and terrorist factions.
Computer systems as well as all their connected devices could be used against us if compromised by someone with malicious intent. IoT will force a fundamental change in how security is implemented by making inventory control and knowledge about the presence of connected entities a priority security requirement.
The author of this blog is Marcel Shaw, federal sales engineer at LANDESK
Comment on this article below or via Twitter @IoTGN

 According to Proofpoint, more than 25% of the botnet was made up of devices other than computers, including smart TVs, a refrigerator, and other household appliances.
According to Proofpoint, more than 25% of the botnet was made up of devices other than computers, including smart TVs, a refrigerator, and other household appliances.